Navigating the Terrain: A Comprehensive Guide to DDoS Attack Maps
Related Articles: Navigating the Terrain: A Comprehensive Guide to DDoS Attack Maps
Introduction
In this auspicious occasion, we are delighted to delve into the intriguing topic related to Navigating the Terrain: A Comprehensive Guide to DDoS Attack Maps. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Navigating the Terrain: A Comprehensive Guide to DDoS Attack Maps

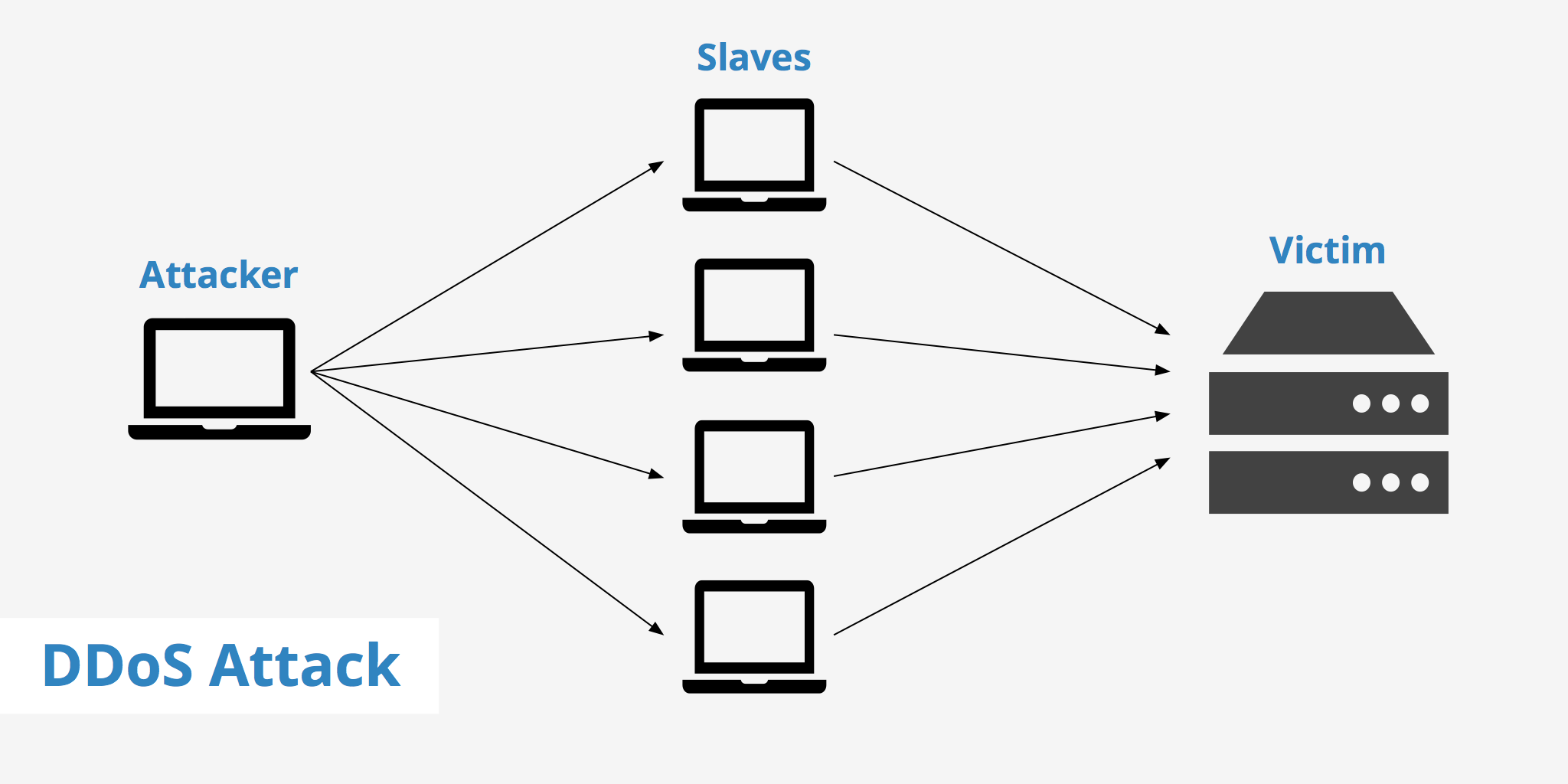
In the ever-evolving landscape of cyber threats, Distributed Denial of Service (DDoS) attacks remain a potent weapon in the arsenal of malicious actors. These attacks aim to overwhelm a target’s online infrastructure, rendering it inaccessible to legitimate users. While the concept of a DDoS attack is straightforward, understanding the intricacies of its execution and the tools used to analyze its impact requires a deeper dive. This is where DDoS attack maps emerge as invaluable tools, offering a visual representation of attack dynamics and providing insights crucial for mitigation and prevention.
Understanding the Landscape: A Visual Representation of Cyber Warfare
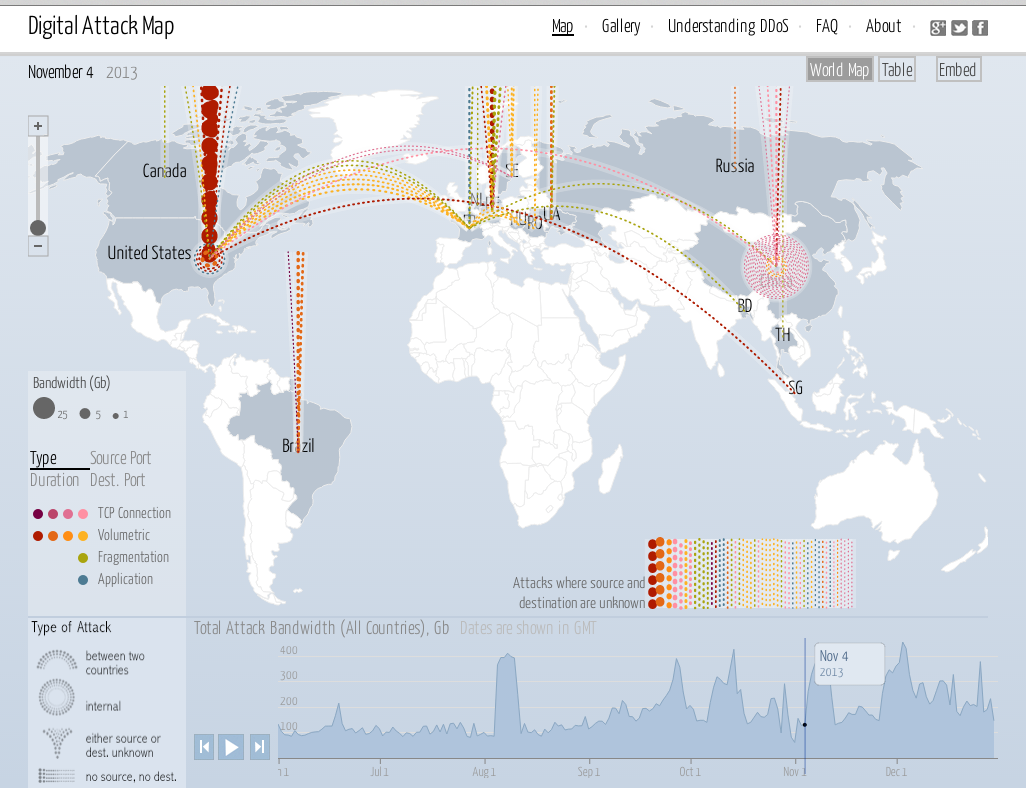
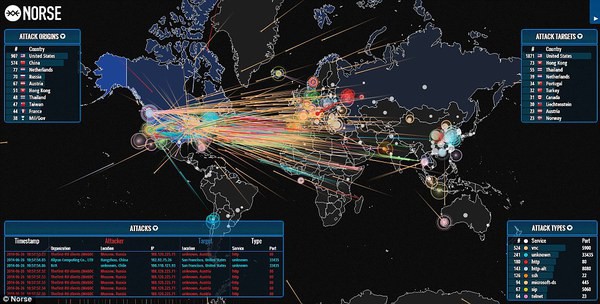
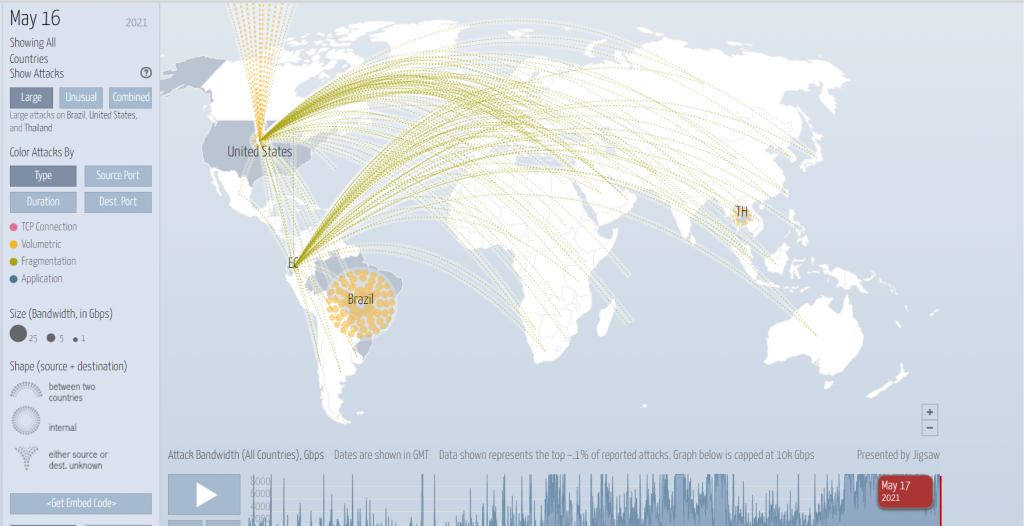
DDoS attack maps serve as visual representations of the global landscape of these cyberattacks. They provide a comprehensive overview of attack origins, targets, and the overall flow of malicious traffic. By visualizing the attack’s trajectory, security professionals gain a deeper understanding of the attack’s scope, the attacker’s tactics, and the potential impact on the target’s network.
Key Components of a DDoS Attack Map:
- Attack Origin: These maps highlight the geographical locations from which the attack originates. This information is crucial for understanding the attacker’s potential motives, resources, and the geographical spread of their botnet.
- Target Location: The map clearly identifies the location of the target organization or service under attack. This helps security teams pinpoint the affected infrastructure and prioritize mitigation efforts.
- Attack Vectors: The map illustrates the various attack vectors employed by the attacker, such as SYN floods, HTTP floods, or DNS amplification attacks. Understanding the attack vector allows security professionals to deploy specific countermeasures tailored to the specific threat.
- Traffic Flow: The map depicts the flow of malicious traffic from the attacker’s botnet to the target’s network. This visualization provides insights into the attack’s intensity, duration, and the attacker’s ability to overwhelm the target’s resources.
- Mitigation Strategies: Some DDoS attack maps incorporate information about the mitigation strategies employed by the target organization. This includes details about the use of firewalls, load balancers, and other security solutions to mitigate the attack’s impact.
The Value of Visualizing the Threat:
DDoS attack maps offer several benefits for security professionals, organizations, and researchers:
- Enhanced Situational Awareness: By visualizing the attack’s trajectory and its impact, security teams gain a real-time understanding of the threat landscape. This allows for quicker decision-making and more effective mitigation strategies.
- Improved Threat Intelligence: DDoS attack maps provide valuable insights into the attacker’s tactics, techniques, and procedures. This information can be used to refine threat intelligence models and predict future attacks.
- Effective Resource Allocation: By understanding the attack’s scope and intensity, security teams can allocate resources effectively to prioritize mitigation efforts and protect critical infrastructure.
- Collaborative Response: DDoS attack maps can facilitate collaboration between organizations and security researchers. Sharing attack data and insights enables a collective response to emerging threats.
- Public Awareness: These maps can be used to educate the public about the nature and impact of DDoS attacks, fostering a greater understanding of cyber threats and the importance of cybersecurity.
Beyond the Map: Utilizing Data for Actionable Insights
While DDoS attack maps provide a visual representation of the threat, their true value lies in the data they contain. By analyzing this data, security professionals can gain actionable insights into the following:
- Attacker Motives: Identifying the attacker’s origin and the targeted organization can shed light on their motives. This information can help organizations understand the potential risks they face and develop targeted mitigation strategies.
- Attack Tactics and Techniques: Analyzing the attack vectors and traffic patterns reveals the attacker’s preferred methods. This knowledge enables security teams to develop countermeasures specifically designed to address those tactics.
- Vulnerability Assessment: By examining the attack’s impact and the areas of the target network most affected, organizations can identify vulnerabilities that need to be addressed.
- Threat Modeling: DDoS attack maps can be used to create threat models, which simulate potential attacks and assess the organization’s preparedness. This allows for proactive security measures and mitigation strategies.
- Post-Attack Analysis: After an attack, the data from DDoS attack maps can be used to analyze the attack’s impact, identify weaknesses in the security infrastructure, and improve future defenses.
FAQs about DDoS Attack Maps
1. What are the limitations of DDoS attack maps?
DDoS attack maps primarily focus on visualizing the attack’s trajectory and impact. They may not provide detailed information about the attacker’s identity, their botnet infrastructure, or the specific techniques used to launch the attack.
2. How can I access DDoS attack maps?
Several organizations and security researchers maintain public DDoS attack maps. These maps are often available online and can be accessed through dedicated websites or research publications.
3. Are DDoS attack maps used only for defense?
While DDoS attack maps are primarily used for defensive purposes, they can also be used by attackers to gain insights into potential targets and vulnerabilities. This highlights the importance of maintaining a strong cybersecurity posture and keeping sensitive data secure.
4. How do DDoS attack maps contribute to cybercrime investigation?
The data gathered from DDoS attack maps can be used by law enforcement agencies to trace the attack’s origin and identify the perpetrators. This information can assist in prosecuting cybercriminals and deterring future attacks.
5. What are the future trends in DDoS attack maps?
As the cyber threat landscape evolves, DDoS attack maps are expected to become more sophisticated and comprehensive. They will likely incorporate real-time data analysis, machine learning algorithms, and advanced visualization techniques to provide even greater insights into attack dynamics.
Tips for Utilizing DDoS Attack Maps Effectively:
- Choose the Right Map: Select a DDoS attack map that aligns with your specific needs and provides the relevant data for your organization.
- Understand the Data: Carefully analyze the information presented on the map, considering its context and limitations.
- Integrate with Other Security Tools: Combine DDoS attack maps with other security tools, such as intrusion detection systems and network monitoring platforms, for a comprehensive view of the threat landscape.
- Share Information: Collaborate with other organizations and security researchers to share information about DDoS attacks and enhance collective defense capabilities.
- Stay Informed: Continuously update your knowledge about DDoS attacks and the latest trends in attack techniques and mitigation strategies.
Conclusion: A Tool for Navigating the Cyber Landscape
DDoS attack maps are invaluable tools for navigating the complex and ever-evolving landscape of cyber threats. They provide a visual representation of attack dynamics, enabling security professionals to gain a deeper understanding of the threat, develop effective mitigation strategies, and enhance their overall cybersecurity posture. By leveraging the insights gleaned from DDoS attack maps, organizations can proactively defend themselves against these devastating cyberattacks and ensure the resilience of their online infrastructure.




Closure
Thus, we hope this article has provided valuable insights into Navigating the Terrain: A Comprehensive Guide to DDoS Attack Maps. We thank you for taking the time to read this article. See you in our next article!